Page 58 - Viva ICSE Computer Studies 7 : E-book
P. 58
4. Hacking done for a good cause _________________
5. Illegal copying of software _________________
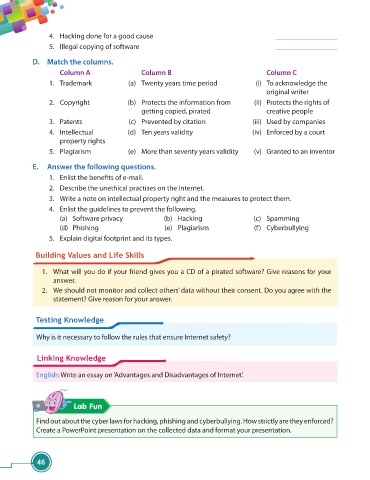
D. Match the columns.
Column A Column B Column C
1. Trademark (a) Twenty years time period (i) To acknowledge the
original writer
2. Copyright (b) Protects the information from (ii) Protects the rights of
getting copied, pirated creative people
3. Patents (c) Prevented by citation (iii) Used by companies
4. Intellectual (d) Ten years validity (iv) Enforced by a court
property rights
5. Plagiarism (e) More than seventy years validity (v) Granted to an inventor
E. Answer the following questions.
1. Enlist the benefi ts of e-mail.
2. Describe the unethical practises on the Internet.
3. Write a note on intellectual property right and the measures to protect them.
4. Enlist the guidelines to prevent the following.
(a) Software privacy (b) Hacking (c) Spamming
(d) Phishing (e) Plagiarism (f) Cyberbullying
5. Explain digital footprint and its types.
Building Values and Life Skills
1. What will you do if your friend gives you a CD of a pirated software? Give reasons for your
answer.
2. We should not monitor and collect others’ data without their consent. Do you agree with the
statement? Give reason for your answer.
Testing Knowledge
Why is it necessary to follow the rules that ensure Internet safety?
Linking Knowledge
English: Write an essay on ‘Advantages and Disadvantages of Internet’.
Lab Fun
Find out about the cyber laws for hacking, phishing and cyberbullying. How strictly are they enforced?
Create a PowerPoint presentation on the collected data and format your presentation.
46